In the modern era of digital transformation, cloud computing is the key to unlocking business agility, scalability, and efficiency. However, with the convenience of cloud services comes the responsibility of safeguarding your cloud environment from unauthorized access and security threats. That’s where Cloud Access Control Systems (CAS) step in as the gatekeepers of your cloud kingdom, ensuring the confidentiality, integrity, and availability of your precious data and applications.
Laying the Foundation: Understanding the Challenges of Cloud Access Control
Before we delve into the details of CAS, let’s acknowledge the inherent challenges that accompany cloud access management. With multiple users, devices, and applications accessing the cloud infrastructure, it becomes increasingly difficult to maintain a consistent level of security. Traditional access control mechanisms, such as firewalls and passwords, fall short in addressing these complexities, leaving your cloud environment vulnerable to unauthorized access and data breaches.
Empowering Control: The Role of Cloud Access Control Systems
Cloud Access Control Systems are the silver bullet to these challenges, providing a comprehensive framework for managing and securing access to cloud resources. These systems empower organizations to define fine-grained access policies, enforce role-based permissions, and monitor and audit user activities. By implementing CAS, organizations can establish clear accountability, prevent unauthorized access, and ensure compliance with industry regulations.

Cloud Access Control – Solution for Security – Source www.getkisi.com
Personal Journey to Cloud Access Control: A Tale of Transformation
I recall a time when our organization faced a severe security breach due to weak access controls. The consequences were devastating, resulting in data loss, reputational damage, and financial penalties. That incident became the catalyst for our journey towards adopting a robust CAS. The implementation process was meticulous, involving collaboration with our IT team, security experts, and business leaders. With careful planning and execution, we deployed a CAS that not only enhanced our security posture but also streamlined our access management processes.
Diving Deeper into Cloud Access Control Systems: Unleashing the Power
CAS encompasses various components that work in harmony to safeguard your cloud environment. Identity and Access Management (IAM) services serve as the cornerstone, enabling organizations to manage user identities, define their roles and permissions, and enforce access policies. Cloud Directory Services provide a centralized repository for storing and managing user and group information, ensuring consistency across cloud applications.

Better cloud access security broker: Securing SaaS cloud apps – Source argonsys.com
History and Mythology: Unveiling the Origins of Cloud Access Control
The concept of access control has its roots in ancient civilizations, where physical barriers and guards protected valuable assets. As technology evolved, access control systems became more sophisticated, transitioning from mechanical locks to electronic keycards and biometric authentication. In the digital realm, the advent of cloud computing necessitated the development of specialized CAS to address the unique challenges of securing cloud environments.
The Hidden Secrets of Cloud Access Control Systems: Unlocking the Mysteries
Beyond the surface, CAS conceals a fascinating array of techniques and technologies that enhance security. Multi-Factor Authentication (MFA) adds an extra layer of protection by requiring users to provide multiple forms of authentication. Single Sign-On (SSO) simplifies access management by allowing users to log in once and gain access to multiple applications. Cloud Access Security Brokers (CASB) provide real-time visibility and control over cloud usage, detecting and preventing security anomalies.

Volo Cloud-Based Access Control | Expert Security UK – Source www.expertsecurityuk.co.uk
Recommendations for Securing Your Cloud with Cloud Access Control Systems
Implementing an effective CAS requires a multifaceted approach. Start by defining clear access policies that align with your organization’s security requirements. Regularly review and update these policies to ensure they remain relevant and effective. Empower your IT team with the necessary training and resources to manage and monitor your CAS effectively. Stay informed about the latest security trends and best practices to keep your cloud environment secure.
Cloud Access Control Systems: A Deeper Dive into the Essentials
To fully grasp the significance of CAS, let’s delve into the underlying principles. Authorization refers to the process of granting or denying access to specific resources based on user identity and permissions. Authentication, on the other hand, verifies the identity of the user attempting to access the resource. CAS also incorporates logging and auditing capabilities, providing a detailed history of user activities for security analysis and compliance purposes.

Securing Access in a Cloud Environment – Source www.comparethecloud.net
Cloud Access Control: Essential Tips for Success
To ensure the effectiveness of your CAS, consider implementing the following tips. Establish a clear governance model that defines roles and responsibilities for access management. Encourage regular security awareness training for employees to promote responsible behavior. Utilize continuous monitoring tools to detect and respond to potential security threats promptly. Stay abreast of industry best practices and emerging technologies to enhance your security posture.
Cloud Access Control: A Holistic Approach to Security
CAS is not merely a technological solution; it represents a cultural shift towards security consciousness. By fostering a culture of accountability and transparency, organizations can create an environment where employees understand their role in protecting the organization’s data and systems. This holistic approach to security, combined with robust CAS implementation, paves the way for a secure and compliant cloud environment.
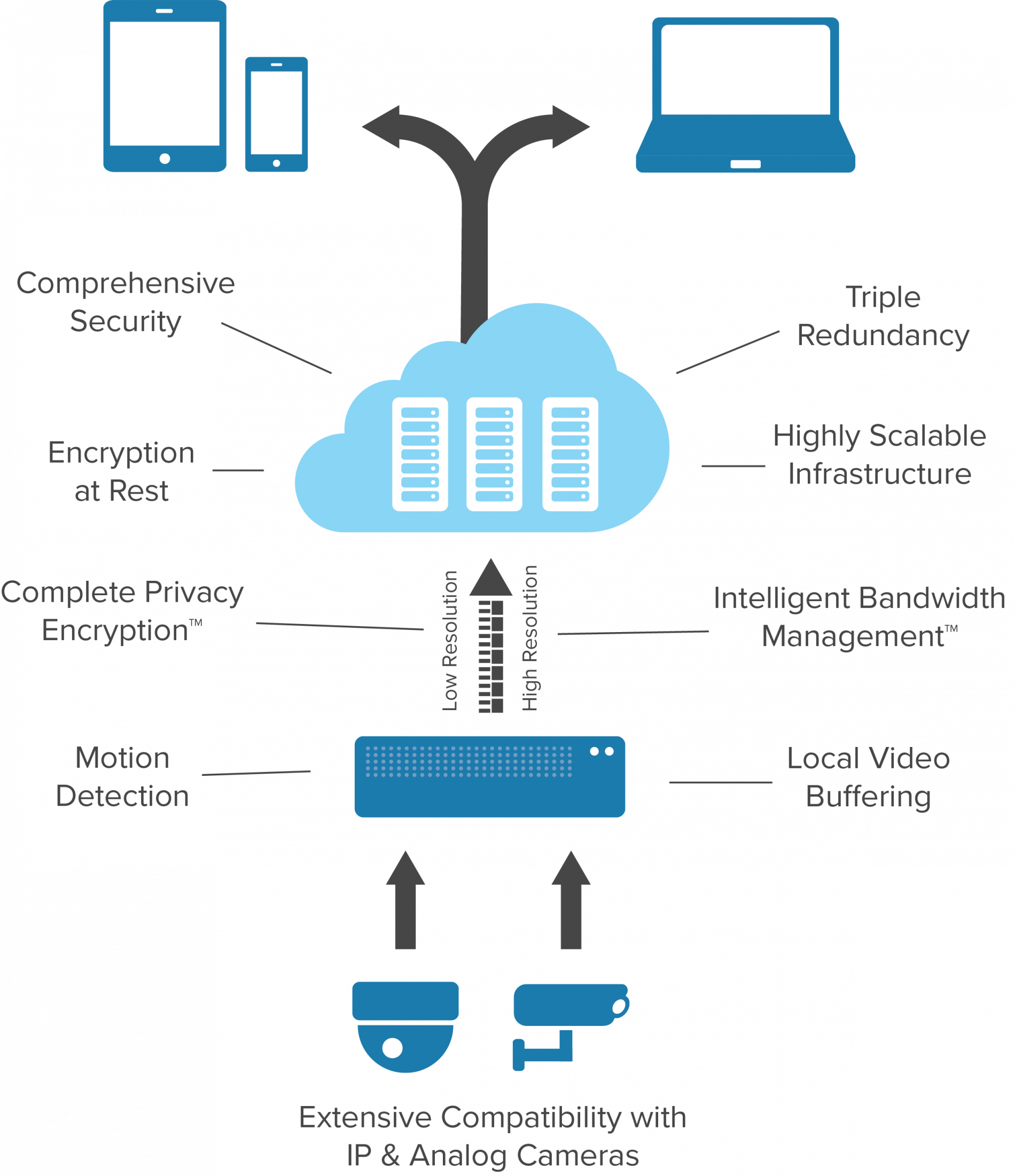
Cloud Security Systems & Solutions | AES Systems, Inc – Source aessystems.com
Fun Facts about Cloud Access Control Systems
Did you know that the first access control system was developed in the 1950s to protect nuclear facilities? Today, CAS is an essential component of cloud security, safeguarding data from potential threats. Some CAS solutions even incorporate advanced AI and machine learning algorithms to detect and prevent sophisticated cyberattacks.
How Do Cloud Access Control Systems Work?
CAS operates on a combination of policies and technologies. It begins with defining access policies that specify who can access what resources and under what conditions. These policies are then translated into rules that are enforced by the CAS. CAS also includes features such as role-based access control (RBAC), which allows administrators to grant access based on predefined roles, and attribute-based access control (ABAC), which allows more granular access control based on specific attributes of the user or resource.

Cloud Access Control System | Easy Storage Solutions – Source www.storageunitsoftware.com
What if Cloud Access Control Systems Fail?
While CAS is a critical component of cloud security, it is not foolproof. If a CAS fails, it can lead to unauthorized access to data and systems. To mitigate this risk, organizations should implement multiple layers of security, including firewalls, intrusion detection systems, and encryption. They should also have a disaster recovery plan in place to ensure that data and systems can be recovered in the event of a CAS failure.
A Listicle of Cloud Access Control System Benefits
Implementing a CAS offers numerous benefits for organizations, including:
- Improved security posture
- Reduced risk of data breaches
- Enhanced compliance
- Simplified access management
- Increased operational efficiency
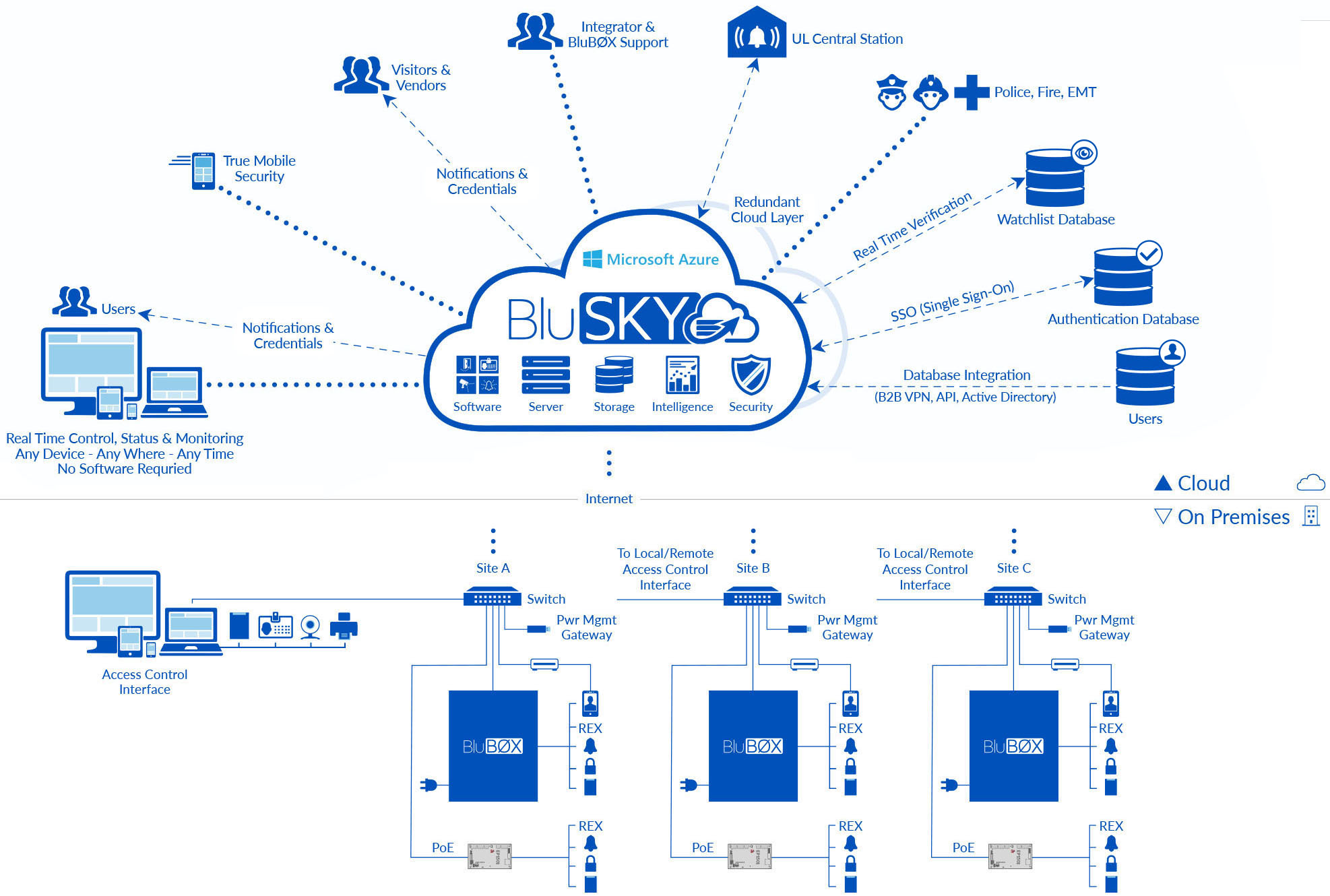
Cloud Access Control – BluINFO – Source knowledge.blub0x.com
Questions and Answers about Cloud Access Control Systems
Q: What are the key components of a CAS?
A: The key components of a CAS include identity and access management (IAM), cloud directory services, and cloud access security brokers (CASB).
Q: What are the benefits of implementing a CAS?
A: Implementing a CAS can improve security posture, reduce the risk of data breaches, enhance compliance, simplify access management, and increase operational efficiency.
Q: How can organizations mitigate the risk of CAS failure?
A: Organizations can mitigate the risk of CAS failure by implementing multiple layers of security, including firewalls, intrusion detection systems, and encryption. They should also have a disaster recovery plan in place.
Q: What are some best practices for implementing a CAS?
A: Best practices for implementing a CAS include defining clear access policies, regularly reviewing and updating policies, empowering IT teams with training and resources, and staying informed about the latest security trends.
Conclusion of Cloud Access Control Systems: Securing Your Cloud Environment
Cloud Access Control Systems are indispensable tools for safeguarding your cloud environment from unauthorized access and security threats. By implementing a robust CAS, organizations can establish a strong foundation for data protection, compliance, and operational efficiency. Embracing the principles and best practices of CAS empowers organizations to navigate the complexities of cloud computing with confidence, ensuring the integrity and security of their valuable assets.
