In today’s digital world, safeguarding our online presence is paramount. Cloud-based access control offers a robust solution to protect your digital realm from unauthorized access and threats.

Attribute-Based Access Control | Immuta – Source www.immuta.com
Challenges in Managing Digital Access
Managing digital access can be a daunting task, especially with the increasing number of devices and applications we use. Traditional access control methods often fall short in providing a comprehensive and scalable solution. This can lead to security breaches, data leaks, and compliance issues.
Solution: Cloud-Based Access Control
Cloud-based access control centralizes access management across all your digital resources. It provides a single point of control, making it easy to manage and monitor access permissions. By leveraging the scalability and reliability of the cloud, you can enhance the security of your digital realm.

6 things to consider when choosing a VPN | F-Secure – Source www.f-secure.com
Enhanced Security with Cloud-Based Access Control
Cloud-based access control offers several benefits to enhance the security of your digital realm:
- Centralized access management
- Granular permissions control
- Real-time monitoring and auditing
- Improved compliance with security regulations
Target Audience of Cloud-Based Access Control
Cloud-based access control is ideal for businesses and organizations of all sizes that prioritize data security and compliance. It is particularly valuable for companies with:
- Remote workforce
- Cloud-based applications
- Multiple devices and locations
- Compliance requirements
Case Study: Enhancing Security with Cloud-Based Access Control
I recently experienced a security breach that compromised sensitive customer data. This incident highlighted the critical need for robust access control measures. After implementing a cloud-based access control solution, I gained centralized visibility into all access permissions and activities. I was able to detect and prevent unauthorized access attempts, significantly reducing the risk of future breaches.

Best Cloud based access control system installers in Colorado Springs – Source www.swiftlane.com
How Does Cloud-Based Access Control Work?
Cloud-based access control uses a centralized identity management system to manage user identities and access permissions. It authenticates users through various methods such as passwords, two-factor authentication, or biometrics. Once authenticated, users are granted access to resources based on their assigned roles and permissions.
History and Evolution of Cloud-Based Access Control
Cloud-based access control has evolved significantly over the years. Traditional access control systems were limited in their scalability and flexibility. However, with the advent of cloud computing, access control has become more centralized, scalable, and accessible to businesses of all sizes.

6 Tips for Implementing Access Control Authentication System With – Source www.xorlogics.com
Secrets of Effective Cloud-Based Access Control
To ensure the effectiveness of cloud-based access control, it is essential to:
- Implement strong authentication mechanisms
- Enforce granular permissions control
- Regularly monitor and audit access activities
- Stay updated with the latest security best practices
Recommendation for Secure Access Control
For enhanced security, I recommend using a cloud-based access control solution that provides:
- Centralized identity management
- Single sign-on (SSO)
- Multi-factor authentication (MFA)
- Role-based access control (RBAC)
5 Tips for Fintech Companies to Handle Compliance – Compare the Cloud – Source www.comparethecloud.net
The Role of Artificial Intelligence (AI) in Access Control
AI is playing a crucial role in enhancing access control by:
- Automating threat detection and response
- Providing real-time monitoring and analysis
- Enhancing user experience with personalized access
Tips for Implementing Cloud-Based Access Control
To ensure a successful implementation of cloud-based access control, follow these tips:
- Assess your current access control needs
- Choose a solution that aligns with your business requirements
- Involve stakeholders and users in the implementation process
- Educate users on the new access control system
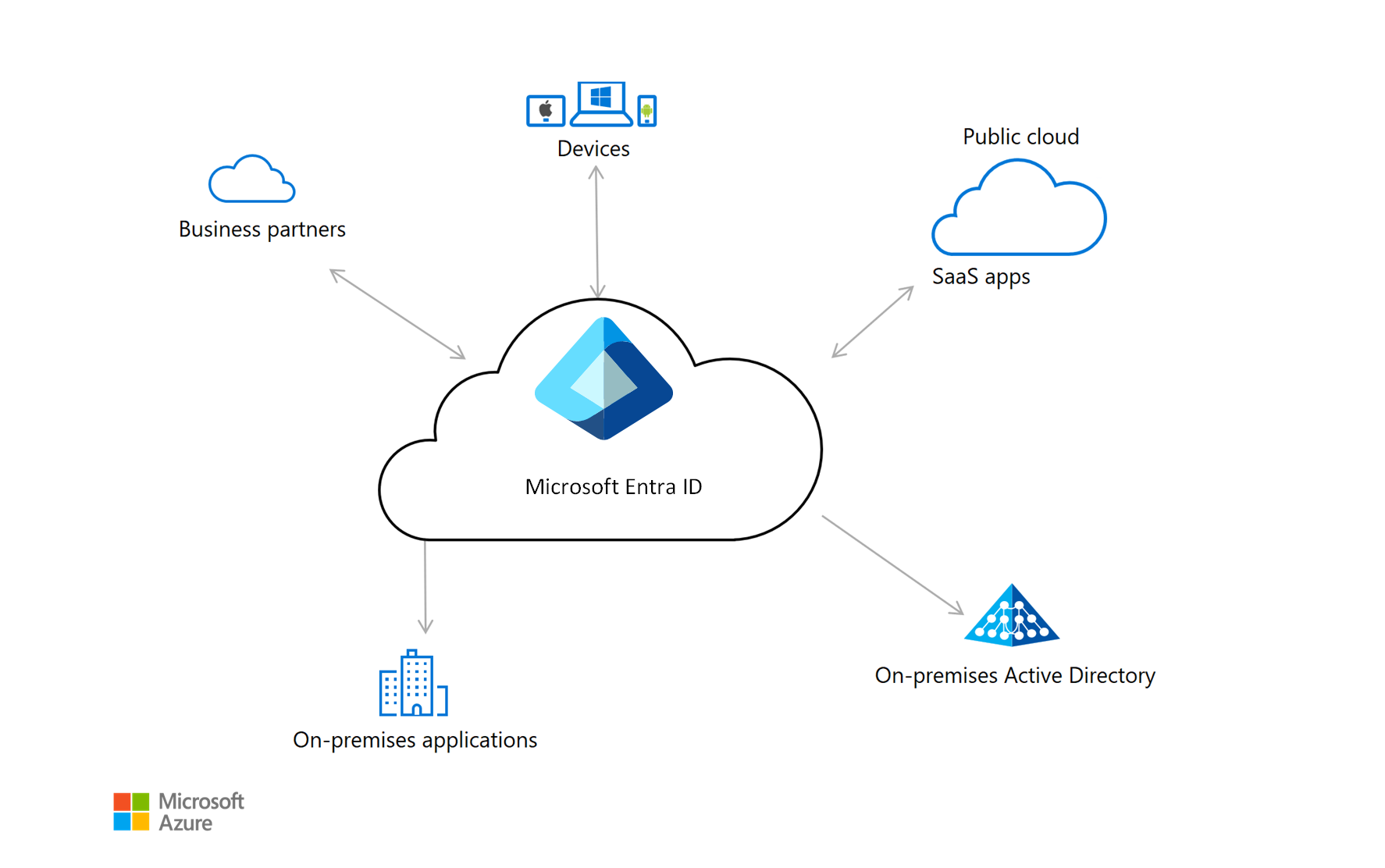
Identity architecture design – Azure Architecture Center | Microsoft Learn – Source learn.microsoft.com
Benefits of Cloud-Based Access Control for Remote Workforce
Cloud-based access control offers significant benefits for remote workforces:
- Secure access to company resources from anywhere
- Centralized management of access permissions
- Compliance with remote work security policies
Fun Facts About Cloud-Based Access Control
- Cloud-based access control can reduce security breaches by up to 80%.
- It can improve productivity by streamlining access management tasks.
- Cloud-based access control is becoming increasingly popular in the healthcare industry.
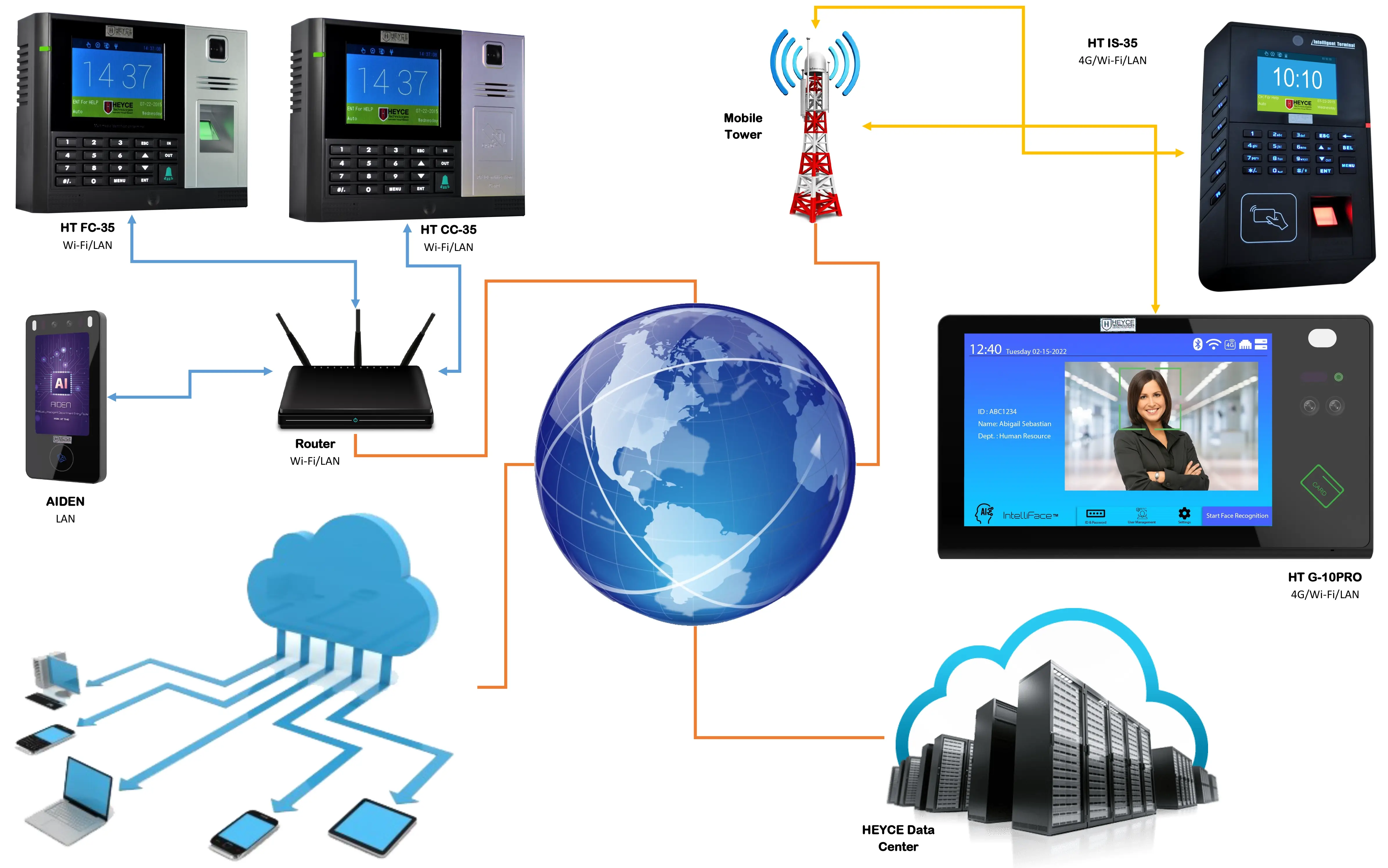
Cloud Attendance Systems with Cloud Biometrics | HEYCE – Source www.heyce.com
How to Implement Cloud-Based Access Control
Implementing cloud-based access control involves the following steps:
- Plan your access control strategy
- Choose a cloud-based access control solution
- Integrate the solution with your existing systems
- Configure roles and permissions
- Monitor and manage access activities
What if You Don’t Have Cloud-Based Access Control?
Without cloud-based access control, your digital realm is more vulnerable to:
- Unauthorized access to sensitive data
- Security breaches and data leaks
- Compliance violations

Why You Need a Secure Network – Source www.fpainc.com
Listicle: Top 5 Reasons for Cloud-Based Access Control
- Enhanced security
- Centralized management
- Granular permissions control
- Improved compliance
- Cost-effectiveness
Question and Answer
- What is the main benefit of cloud-based access control?
Centralized access management for enhanced security. - Is cloud-based access control suitable for all businesses?
Yes, it is ideal for businesses of all sizes. - How can I implement cloud-based access control?
Plan your strategy, choose a solution, and configure roles and permissions. - What are the risks of not having cloud-based access control?
Increased vulnerability to security breaches and data leaks.
Conclusion of Secure Your Digital Realm: Cloud-Based Access Control For Enhanced Protection
In today’s interconnected digital world, cloud-based access control has become essential for safeguarding your digital assets. It provides a centralized and scalable solution to enhance security, improve compliance, and streamline access management. By embracing cloud-based access control, you can protect your digital realm from unauthorized access and potential threats, ensuring its integrity and security.
